Consider the following set of flowcharting symbols along with the case as you respond to the next question: When the CEO of NTL Corporation resigned, the board of directors hired a recruitment firm to look for a replacement. The recruitment firm prepared several job announcements, then presented them to the board of directors. The board of directors approved one of the job announcements; the recruitment firm used it to advertise the position on the Internet and in relevant newspapers and professional publications. After receiving several applications, the recruitment firm selected a pool of ten to pass on to NTL's board of directors. The board of directors, with the assistance of the recruitment firm, went through three rounds of interviews, narrowing the pool from ten to three. Each of the three finalists prepared a presentation on the strategic future of NTL and delivered the presentation at a meeting of NTL shareholders. The board of directors then made the final choice for a new CEO. 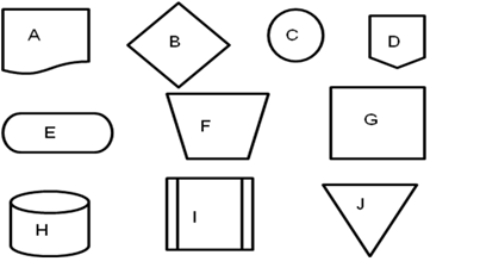 If the "recruiting firm" column of a systems flowchart includes a predefined process labeled "receive applications," it is likely to be connected to:
If the "recruiting firm" column of a systems flowchart includes a predefined process labeled "receive applications," it is likely to be connected to:
Definitions:
System of Linear Equations
A set of one or more linear equations that share the same variables.
Interest Rate
A percentage representing the cost of borrowing money or the return on investment for savings.
Annual Payment
A payment made once every year, often related to loans, annuities, or other financial products.
Lenders
Entities or individuals that provide funds to borrowers under the condition of future repayment, often with interest.
Q1: The CoBIT framework can be used to
Q2: Consider the following short case as you
Q2: At HCK Corporation, only employees in the
Q6: Consider the independent statements below. Organize them
Q16: As a form of internal control to
Q18: Maher and Maher proposed that the real
Q19: Consider the following statements as you respond
Q23: Cultural biases are generally not problematic in
Q25: Which of the following should be placed
Q44: Consider the following examples of computer crime