Find the distance around the figure below by using the appropriate formula, if 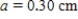 ,
, 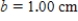 ,
, 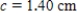 ,
, 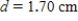 ,
, 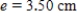 . Round approximate answers to two decimal places.
. Round approximate answers to two decimal places. 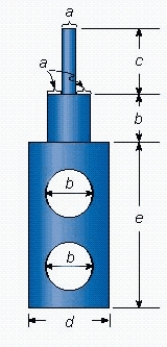
Definitions:
User Action
Any interaction a user makes with a software or a digital interface, such as clicking a button, entering data, or navigating through a website.
Copyright Protection
Legal rights given to the creators of original works, protecting them against unauthorized use or distribution of their work.
Life+70
A term referring to copyright duration, extending copyright protection for the life of the author plus 70 years.
Botnet
A network of computers that have been compromised by, and under control of, a hacker, who is called the botmaster.
Q16: How much coffee does an average cup
Q24: Find the perimeter by using the appropriate
Q34: The first draft of a research paper
Q34: Water boils at what temperature? <br>A) 100
Q64: A(n) green wavy underline indicates the text
Q65: Does the picture below illustrate the line
Q71: Microsoft OneNote is a _ app for
Q106: Change the given form into the decimal
Q121: What is the sum of the first
Q143: Factor the expression completely.<br> <img src="https://d2lvgg3v3hfg70.cloudfront.net/TB7816/.jpg" alt="Factor