Use the following to answer questions:
Figure: Imposition of a Tax 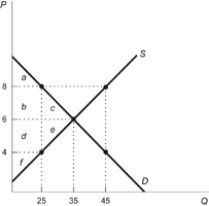
-(Figure: Imposition of a Tax) Refer to the figure. After the imposition of a $4 tax, the government collects revenues of:
Definitions:
Vulnerability
A weakness or gap in security that can be exploited by threats to gain unauthorized access to an asset.
SCADA Attacks
Cyber attacks targeting Supervisory Control and Data Acquisition systems, which are crucial for industrial control systems, potentially disrupting critical infrastructure.
User Access
The permission or rights granted to users to make use of a system, network, or specific resources within them.
Risk Transference Strategy
A tactic used in risk management where the potential impact of a risk is shifted to a third party, often through insurance or outsourcing.
Q18: Ceteris paribus, the total subsidy is largest
Q20: (Figure: Gun Market) In the gun market
Q31: The war on drugs has caused the
Q33: Figure: Two Demand Curves <img src="https://d2lvgg3v3hfg70.cloudfront.net/TB33781/.jpg" alt="Figure:
Q37: MOST economies today are<br>A) centrally planned.<br>B) market
Q43: (Figure: Tax on Consumers of Gadgets) Refer
Q80: A market is a form of:<br>A) decentralized
Q145: If the price elasticity of demand is
Q197: If the demand for a good is
Q229: Which good below might be expected to