Artificial hip joints consist of a ball and socket. As the joint wears, the ball (head) becomes rough. Investigators performed wear tests on metal artificial; hip joints. Joints with several different Diameters were tested. The following table presents measurements of head roughness (in Nanometers) . 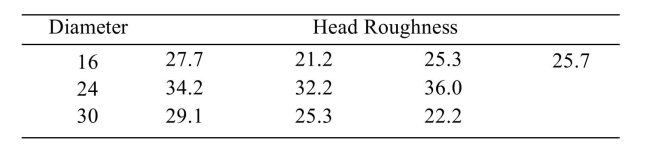 Perform the Tukey-Kramer test to determine which pairs of means, if any, differ. Use the level of Significance.
Perform the Tukey-Kramer test to determine which pairs of means, if any, differ. Use the level of Significance.
Definitions:
Integrated Circuits
A set of electronic circuits on one small flat piece (or "chip") of semiconductor material, usually silicon.
Information Security
The practice of preventing unauthorized access, use, disclosure, disruption, modification, inspection, recording, or destruction of information.
Hackers
Individuals who use their technical knowledge to gain unauthorized access to computer systems for various purposes, ranging from malicious attacks to ethical hacking.
Viruses
Malicious software programs designed to infect and harm computers, often by replicating themselves or stealing information.
Q3: Construct a boxplot for the data
Q4: Let A and B be events
Q10: The following display from a TI-84
Q14: The following table presents the numbers
Q31: A firm wants to strengthen its financial
Q36: The following table presents the purchase
Q41: For this year's mayoral election, voter dissatisfaction
Q49: One problem with ratio analysis is that
Q62: A Karate club consists of 54 persons
Q64: Suppose you are the president of a