Solve: 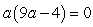
Definitions:
Phishing Attack
A fraudulent attempt to obtain sensitive information such as usernames, passwords, and credit card details by disguising oneself as a trustworthy entity in electronic communication.
Different Passwords
The use of unique passwords for different accounts or services to enhance security and minimize the risk of unauthorized access.
Gibberellins
A group of plant hormones that stimulate stem elongation, germination, and flowering among other developmental processes.
Carpel
The female reproductive organ of a flower, encompassing the ovary, style, and stigma.
Q2: What form might a report to the
Q7: Suppose that a firm's production function is
Q28: Simplify: <img src="https://d2lvgg3v3hfg70.cloudfront.net/TB8311/.jpg" alt="Simplify: A)
Q41: Graph: <img src="https://d2lvgg3v3hfg70.cloudfront.net/TB8311/.jpg" alt="Graph: A)
Q49: Simplify: <img src="https://d2lvgg3v3hfg70.cloudfront.net/TB8311/.jpg" alt="Simplify: A)
Q57: Simplify: <img src="https://d2lvgg3v3hfg70.cloudfront.net/TB8311/.jpg" alt="Simplify: A)
Q68: Factor: <img src="https://d2lvgg3v3hfg70.cloudfront.net/TB8311/.jpg" alt="Factor: A)
Q75: Simplify: <img src="https://d2lvgg3v3hfg70.cloudfront.net/TB8311/.jpg" alt="Simplify: A)
Q78: An isosceles triangle has two sides of
Q86: Find the x- and y-intercepts of the