Consider the function 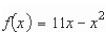 and the point
and the point 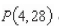 n the graph of
n the graph of
Definitions:
Rainbow Table
A security attack method used to obtain a password in a shorter amount of time because the attacker has a table that contains previously discovered hash values.
TCP/IP Hijacking
A type of cyber attack on the Transmission Control Protocol/Internet Protocol, where the attacker takes over a web session between two computers.
Spoofing
A malicious practice where an attacker impersonates another device or user on a network, aiming to deceive systems or individuals for unauthorized access or data theft.
Social Engineering
The art of manipulating people so they give up confidential information or perform actions they wouldn't normally consider.
Q10: Which of the following is a solution
Q18: Suppose that the population (in millions) of
Q26: Match the equation with its graph. <img
Q30: To carry a 500-pound cylindrical weight, two
Q32: Find the indefinite integral <img src="https://d2lvgg3v3hfg70.cloudfront.net/TB8202/.jpg" alt="Find
Q36: Set up and evaluate a double integral
Q71: Which of the following graphs is the
Q77: For which positive integers k is the
Q100: Approximate the sum to the indicated accuracy.
Q101: Find the length of the polar curve.