Figure 3-16 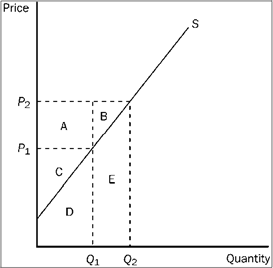
Refer to Figure 3-16. When the price is P 1, producer surplus is
Definitions:
Spear Phishing
A targeted type of social engineering in which the attackers know some information about someone that lulls them into thinking an email or other electronic message is safe.
Legitimate Source
A trusted and credible origin or provider of information, goods, or services, often verified through established reputation or credentials.
Personal Information
Any information related to an identifiable individual, including names, addresses, phone numbers, and email addresses.
Ransomware
A security situation in which a hacker has restricted access to a device until the user is pressured to pay money to regain access.
Q73: Which of the following is an implication
Q105: The production possibilities curve illustrates the basic
Q141: Which of the following would tend to
Q147: The maximum price that consumers are willing
Q207: When an economy is operating efficiently, the
Q307: Bill is willing to cut lawns for
Q362: To be economically successful, the entrepreneur must<br>A)
Q428: If coffee and cream are complements, a
Q510: Figure 3-19 <img src="https://d2lvgg3v3hfg70.cloudfront.net/TBX9057/.jpg" alt="Figure 3-19
Q526: Other things constant, a decrease in consumer