Use the rule for order of operations to simplify the expression as much as possible. 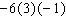
Definitions:
Information Security Controls
Measures implemented to safeguard information by ensuring its confidentiality, integrity, and availability.
Identity Theft
The fraudulent acquisition and use of a person's private identifying information, usually for financial gain.
Financial Information
Data concerning the financial health, performance, and transactions of an individual, business, or other entity, often used for analysis and decision-making.
Unauthorized Access
The gain of entry into a computer system or network without permission.
Q1: A 3-foot 6 inch long rectangular duct
Q5: When subtracting two numbers it is sometimes
Q24: Graph the line with the given slope
Q38: Apply the distributive property. Simplify when possible.
Q92: Solve the equation. <img src="https://d2lvgg3v3hfg70.cloudfront.net/TBX8808/.jpg" alt="Solve the
Q96: Find the solution for the equation. <img
Q147: Graph the solution set for the equation.
Q185: Reduce the fraction to lowest terms. <img
Q206: Solve the equation. <img src="https://d2lvgg3v3hfg70.cloudfront.net/TBX8808/.jpg" alt="Solve the
Q253: Solve the equation. <img src="https://d2lvgg3v3hfg70.cloudfront.net/TBX8808/.jpg" alt="Solve the