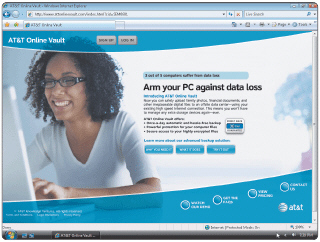
 Figure 7-3 Users who subscribe to disk-based storage like the kind advertised in Figure 7-3 can save on the Internet hard disk in the same manner they save on their local hard disk.
Figure 7-3 Users who subscribe to disk-based storage like the kind advertised in Figure 7-3 can save on the Internet hard disk in the same manner they save on their local hard disk.
Definitions:
Identity Thieves
Criminals who steal personal information to commit fraud or other crimes, often leading to financial loss and damage to the victim's credit.
Cyberporn
Pornographic content available over the internet, accessible through various digital devices and platforms.
Identity Theft
The fraudulent acquisition and use of a person's private identifying information, usually for financial gain.
Cyberterrorism
The use of computer technology to conduct terrorist activities by deliberately disrupting, damaging, or destroying information systems or networks to achieve political or ideological ends.
Q23: One sign of a virus infection is
Q24: In a fiber-optic cable, each strand, called
Q26: <img src="https://d2lvgg3v3hfg70.cloudfront.net/TBX8777/.jpg" alt=" Figure 6-1 When
Q61: _ is a type of DSL that
Q143: A command is _.<br>A) a collection of
Q144: A type of communications device that connects
Q149: Because the best analog televisions have a
Q152: As a user moves a mouse, the
Q160: The _ is the user most likely
Q164: Because LCD projectors tend to produce lower-quality