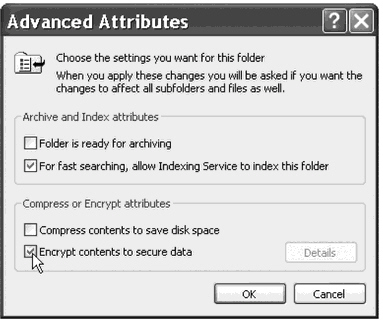
 What form of encryption is being enabled in the figure above?
What form of encryption is being enabled in the figure above?
Definitions:
Attacker
An individual, group, or entity that attempts to gain unauthorized access to computer systems, networks, or data, often with malicious intent.
Demands Payment
A request for the payment of due money, often in the context of bills or services rendered.
Programmer
An individual who writes computer software by writing code in various programming languages.
Trojan Horse
A malicious software that misleads users about its true intent, typically creating a backdoor in a computer system.
Q23: What six tasks do routers perform?
Q26: Up to seven Bluetooth devices can be
Q27: Can routers filter packets on the basis
Q29: The _ communicates with the BIOS, device
Q49: In addition to the folder and file
Q53: Disk quotas reduce the risk that a
Q58: TCP (and UDP) _ software may be
Q74: Are network classes A through C intended
Q82: List five needs are wireless networks are
Q166: _ consists of materials or substances capable