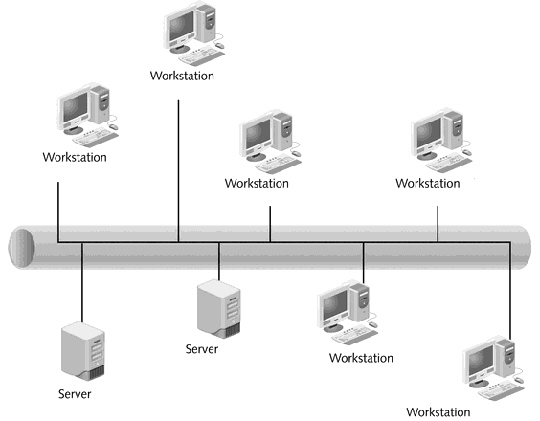
 If a network administrator wants to use host-based intrusion detection, which devices in the figure above would need to be configured?
If a network administrator wants to use host-based intrusion detection, which devices in the figure above would need to be configured?
Definitions:
CRM System
Customer Relationship Management system; a technology for managing all your company's relationships and interactions with customers and potential customers.
Knowledge Management
The process of capturing, distributing, and effectively using knowledge within an organization.
Virtual Office
A service that provides a business with a physical address and office-related services without the need for a dedicated physical space.
Efficient
Achieving maximum productivity with minimum wasted effort or expense, often relating to the effective operation of a process or system.
Q5: Many designers like to use address blocks
Q21: Do not mix several different font _
Q23: What is the maximum downstream transmission speed
Q26: You can use descriptive words such as
Q26: EBlock works with Microsoft's Internet Mail Service
Q37: Sending a malicious SMTP message from a
Q64: What two things can an attacker do
Q71: Page headings traditionally appear in _.
Q78: The opening anchor tag must contain a(n)
Q78: Priority-based access is intended for communications that