Click the Exhibit button. 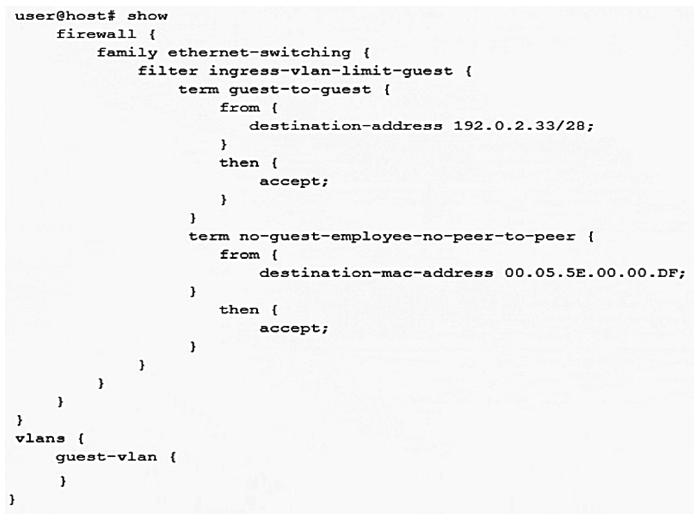 A recent security audit indicates that peer-to-peer applications are allowed on the guest VLAN and employees may have been using the guest VLAN for this purpose. You deploy the configuration shown in the exhibit, but it does not stop the peer-to-peer traffic. In this scenario, what must you do to implement the security policy?
A recent security audit indicates that peer-to-peer applications are allowed on the guest VLAN and employees may have been using the guest VLAN for this purpose. You deploy the configuration shown in the exhibit, but it does not stop the peer-to-peer traffic. In this scenario, what must you do to implement the security policy?
Definitions:
Q25: Referring to the exhibit, not all routes
Q26: Which HTTP status code indicates a response
Q27: Which protocol is used between VCF member
Q30: Click the Exhibit button. <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1585/.jpg" alt="Click
Q31: What are two networking components of OpenStack?
Q31: You are designing a Layer 2 fabric
Q38: Which statement is true about a Data
Q48: What is a type of security feed
Q70: Click the Exhibit button. <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1585/.jpg" alt="Click
Q104: When configuring firewall filters, which function does