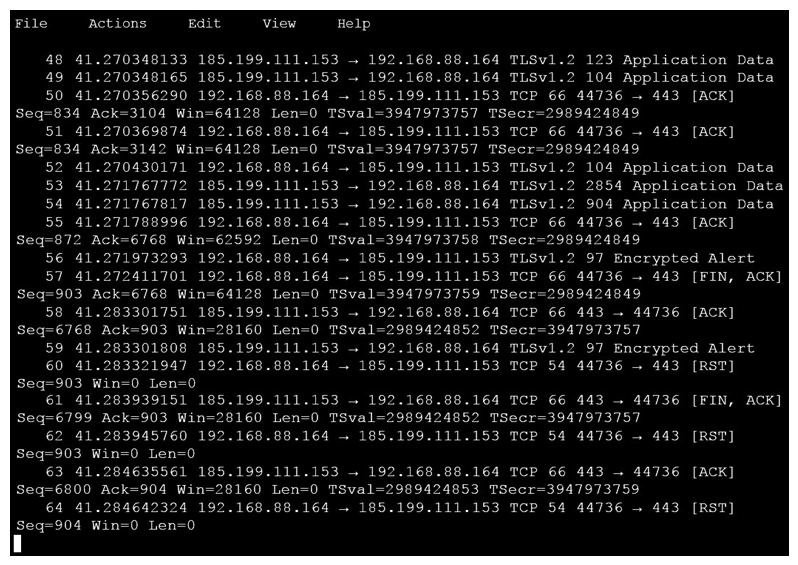
 An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture the analyst cannot determine the technique and payload used for the communication. Which obfuscation technique is the attacker using?
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture the analyst cannot determine the technique and payload used for the communication. Which obfuscation technique is the attacker using?
Definitions:
Direct Method
A technique used in cost accounting to allocate service department costs directly to production departments without considering service department interactions.
Operating Activities
The day-to-day tasks involved in managing a business which include production, sales, and the purchase of inventory.
Cash Dividends
A distribution of a company's earnings to shareholders in the form of cash payments.
Direct Method
A way of preparing a cash flow statement where actual cash inflows and outflows from operational activities are listed directly.
Q27: Which type of memory stores the decompressed
Q44: Storage virtualization is commonly used for SANs
Q73: What should a security analyst consider when
Q138: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q139: Which two actions influence the EIGRP route
Q174: When should a change request be submitted
Q180: Refer to the exhibit. Which configuration issue
Q264: Which option about JSON is true<br>A) uses
Q289: Which two options are the best reasons
Q325: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the