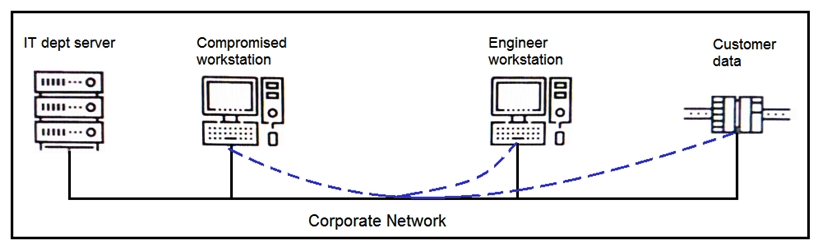
 Refer to the exhibit. An engineer received a report that an attacker has compromised a workstation and gained access to sensitive customer data from the network using insecure protocols. Which action prevents this type of attack in the future?
Refer to the exhibit. An engineer received a report that an attacker has compromised a workstation and gained access to sensitive customer data from the network using insecure protocols. Which action prevents this type of attack in the future?
Definitions:
Debug
The process of identifying and removing errors or bugs from software or hardware to ensure correct operation and functionality.
Visible Property
A setting in software development that controls whether an element or control is displayed to the user.
Program Flow
Refers to the order in which individual statements, instructions, or function calls of an imperative or a structured program are executed or evaluated.
Action Catalog
A collection or listing of actions or commands that can be utilized within an application or software environment.
Q1: A DevOps engineer has built a new
Q9: When a Cisco Webex Video Mesh Node
Q31: Which feature must be configured to allow
Q44: CollabCorp is a global company with two
Q65: Which two configuration parameters are prerequisites to
Q65: The incident response team was notified of
Q69: Refer to the exhibit. <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt="Refer
Q72: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q80: Refer to the exhibit. A security analyst
Q146: Refer to the exhibit. <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt="Refer