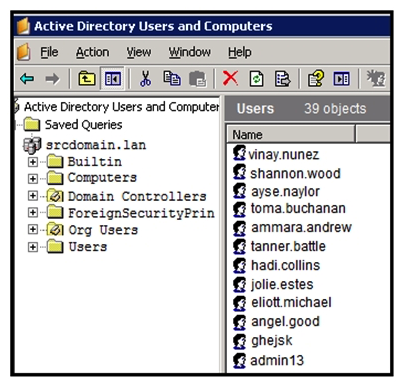
 Refer to the exhibit. An engineer is investigating a case with suspicious usernames within the active directory. After the engineer investigates and cross-correlates events from other sources, it appears that the 2 users are privileged, and their creation date matches suspicious network traffic that was initiated from the internal network 2 days prior. Which type of compromise is occurring?
Refer to the exhibit. An engineer is investigating a case with suspicious usernames within the active directory. After the engineer investigates and cross-correlates events from other sources, it appears that the 2 users are privileged, and their creation date matches suspicious network traffic that was initiated from the internal network 2 days prior. Which type of compromise is occurring?
Definitions:
Dominant Buddhism
Refers to regions or societies where Buddhism is the most prevalent or influential religion.
Mandala
Sanskrit term for the sacred diagram of the universe; Japanese, mandara.
Borobudur
A 9th-century Mahayana Buddhist temple in Java, Indonesia, featuring a monumental step pyramid structure adorned with elaborate reliefs.
Sacred Form
An object, design, or structure treated with reverence or considered holy within a particular spiritual or religious context.
Q4: What is the purpose of the Call
Q6: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q13: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q19: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q54: A company's web server availability was breached
Q107: An engineer is asked to use SaaS
Q112: Where is the witness deployed in a
Q143: What is a benefit of deploying an
Q152: In a wireless network environment, what is
Q254: An engineer must configure interface GigabitEthernet0/0 for