Multiple Choice
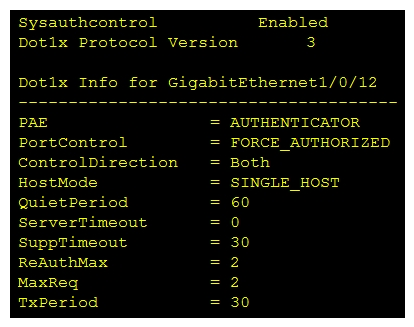 Refer to the exhibit. Which command was used to display this output?
Refer to the exhibit. Which command was used to display this output?
Recognize the importance of environmental factors and community infrastructure in disease prevention.
Understand the historical development of public health initiatives and their impact on community health.
Analyze the role of government and non-governmental organizations in the advancement of public health.
Identify key figures and their contributions to public health and nursing.
Definitions:
Related Questions
Q26: Which exfiltration method does an attacker use
Q36: When configuring Cisco UCM, which configuration enables
Q52: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q79: Which ASA deployment mode can provide separation
Q97: While developing an application following the 12-factor
Q102: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q133: Which encryption hashing algorithm does NTP use
Q137: There is a requirement to securely store
Q188: A network architect must redesign a data
Q232: Which option describes the effect of the