A security engineer noticed an anomaly within a company EC2 instance as shown in the image. The engineer must now investigate what is causing the anomaly. 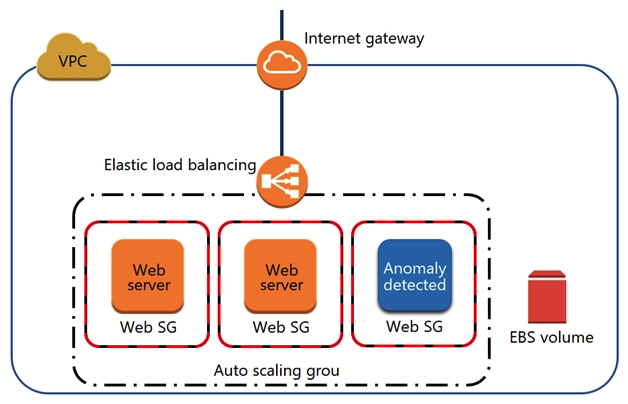 What are the MOST effective steps to take to ensure that the instance is not further manipulated, while allowing the engineer to understand what happened?
What are the MOST effective steps to take to ensure that the instance is not further manipulated, while allowing the engineer to understand what happened?
Definitions:
Computerized Scheduling
The use of computer programs and software to organize appointments, tasks, or events, improving efficiency and accuracy over traditional scheduling methods.
Stream Scheduling
A method used in computing and broadcasting for organizing data processing or transmission according to a predetermined sequence or time.
Time-specified Scheduling
An appointment system where patients are given specific times for their visits, aiming to reduce waiting periods and streamline the process.
Double-booking System
A method used in accounting that records each transaction in two accounts to ensure the balance sheet remains balanced.
Q1: A Security Engineer launches two Amazon EC2
Q67: A company runs a web service on
Q122: The displayed graph is from a forecasting
Q127: A security engineer has enabled AWS Security
Q133: A solutions architect wants all new users
Q290: A developer is planning to use an
Q336: A developer is automating a new application
Q353: A company maintains a searchable repository of
Q440: A development team needs to host a
Q442: A company has an application running on