A security engineer successfully exploits an application during a penetration test. As proof of the exploit, the security engineer takes screenshots of how data was compromised in the application. Given the information below from the screenshot. 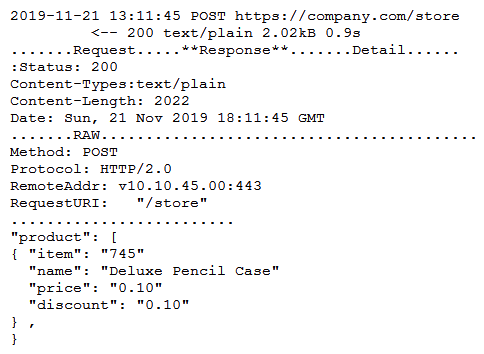 Which of the following tools was MOST likely used to exploit the application?
Which of the following tools was MOST likely used to exploit the application?
Definitions:
Cost-Volume-Profit
An analysis tool used to determine how changes in costs and volume affect a company's operating income and net income.
Sales Volume
The total quantity of products or services sold by a company during a specific period of time.
Contribution Margin Ratio
The percentage of each sales dollar that contributes to covering fixed costs and generating profit.
Products
Goods or services that are created through a business process and offered in the market to satisfy the needs or wants of customers.
Q3: A penetration tester noticed special characters in
Q10: A contract that defines the quality and
Q64: A security team wants to make SaaS
Q132: A medical facility wants to purchase mobile
Q155: A user received a brand new mobile
Q239: Given the following code snippet: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1257/.jpg"
Q259: A technician is restoring files, which were
Q264: A security analyst receives an email from
Q321: Which of the following security principles help
Q374: Which of the following Windows versions introduced