An information security officer is responsible for one secure network and one office network. Recent intelligence suggests there is an opportunity for attackers to gain access to the secure network due to similar login credentials across networks. To determine the users who should change their information, the information security officer uses a tool to scan a file with hashed values on both networks and receives the following data: 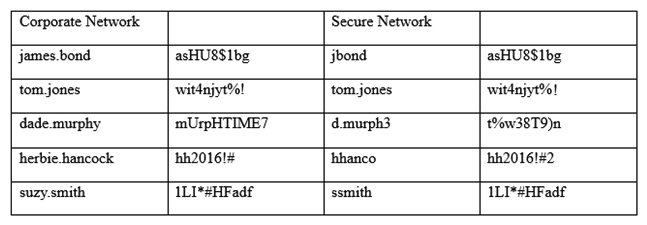 Which of the following tools was used to gather this information from the hashed values in the file?
Which of the following tools was used to gather this information from the hashed values in the file?
Definitions:
Michelle Obama
Former First Lady of the United States, known for her advocacy on poverty awareness, education, nutrition, physical activity, and healthy eating.
Political Affiliation
A person's alignment or association with a particular political party or ideology, reflecting their political beliefs and preferences.
Gender
Socially constructed roles, behaviors, expressions, and identities of girls, women, boys, men, and gender diverse people, distinguished from sex, which is based on physical and biological characteristics.
Outgroup Members
Individuals or groups perceived as not belonging to one's own group, which can affect attitudes and behavior towards them.
Q47: A network engineer is attempting to design-in
Q55: A security analyst is reviewing packet captures
Q107: A penetration tester has been contracted to
Q110: A security appliance vendor is reviewing an
Q127: A security analyst is investigating a malware
Q161: A software development company lost customers recently
Q235: A company's existing forward proxies support software-based
Q247: A new company policy states that all
Q307: A computer running Windows 7 has an
Q415: An organization has employed the services of