A security engineer successfully exploits an application during a penetration test. As proof of the exploit, the security engineer takes screenshots of how data was compromised in the application. Given the information below from the screenshot. 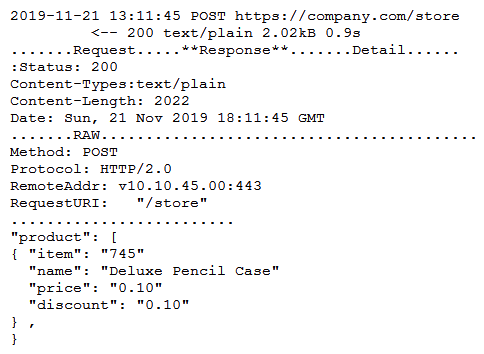 Which of the following tools was MOST likely used to exploit the application?
Which of the following tools was MOST likely used to exploit the application?
Definitions:
Further Action
Implies steps or measures that need to be taken following an initial action, review, or assessment.
Subject Lines
The title or heading of an email or memo that summarizes its content or purpose.
Positive Wording
The use of language that conveys optimism, affirmation, or a positive perspective, often used to encourage constructive outcomes or perceptions.
Purpose Statement
A declaration that outlines the objectives or goals of a document, presentation, or project.
Q18: After performing an initial assessment of a
Q20: A software development manager is running a
Q37: A SaaS provider specifies in a user
Q101: During a security assessment, activities were divided
Q120: During an investigation, a security analyst identified
Q209: A company wants to perform analysis of
Q226: A user is working on a shared
Q290: In which of the following operating systems
Q366: Two new technical SMB security settings have
Q371: A user's computer was infected with malware,