An organization was alerted to a possible compromise after its proprietary data was found for sale on the Internet. An analyst is reviewing the logs from the next-generation UTM in an attempt to find evidence of this breach. Given the following output: 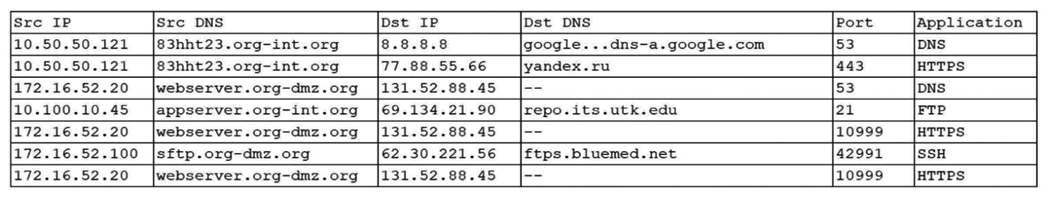 Which of the following should be the focus of the investigation?
Which of the following should be the focus of the investigation?
Definitions:
Q7: An information security analyst is reviewing backup
Q10: A security analyst is building a malware
Q26: A cloud administrator configures a server to
Q30: An information security analyst on a threat-hunting
Q45: Company A has acquired Company B and
Q57: A company has an in-house-developed application. The
Q92: Which of the following cloud principles will
Q130: A consultant is helping a gaming-as-a-service company
Q220: A cloud architect is tasked with isolating
Q223: Which of the following would be appropriate