A penetration tester identifies the following findings during an external vulnerability scan: 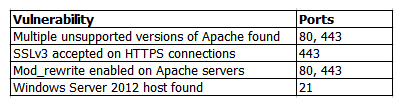 Which of the following attack strategies should be prioritized from the scan results above?
Which of the following attack strategies should be prioritized from the scan results above?
Definitions:
Significant Others
Individuals who hold important places in one’s life and have significant influence, such as family members, close friends, or romantic partners.
Business Ethics
The study of appropriate business policies and practices regarding potentially controversial subjects like corporate governance, insider trading, bribery, discrimination, and corporate social responsibility.
Unethical Situations
Scenarios or conditions where actions or decisions violate moral principles or standards of conduct, often leading to harm or unfairness.
Q45: A penetration tester wants to scan a
Q48: A project manager at a projectized organization
Q49: Which of the following CPU registers does
Q99: A penetration test was performed by an
Q181: Which of the following documents are considered
Q252: Which of the following are mutually binding
Q314: Which of the following events would MOST
Q415: An administrator decides to implement access control
Q561: Which of the following allows virtual machines
Q615: A company is being audited by its