Click the exhibit button. 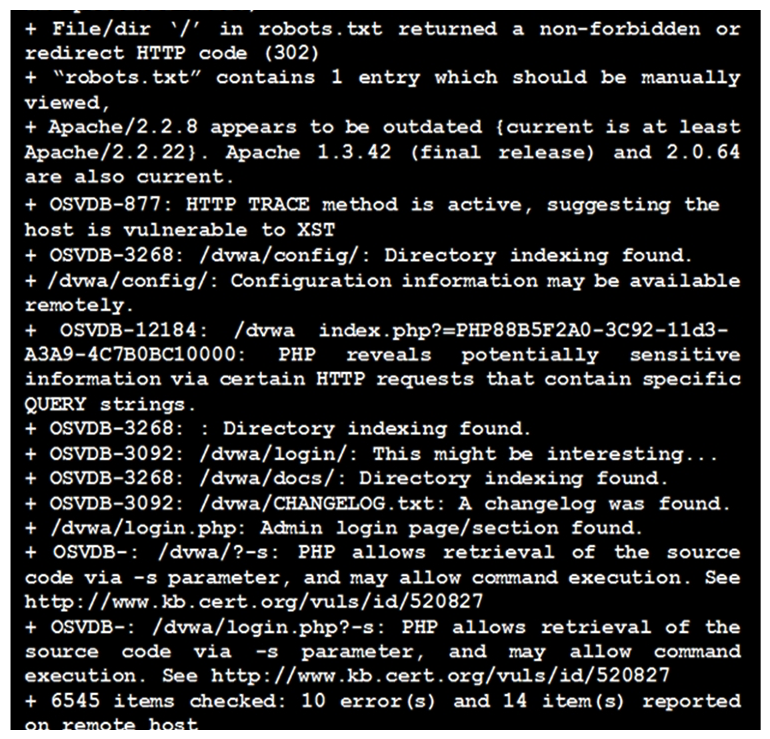 Given the Nikto vulnerability, scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Choose two.)
Given the Nikto vulnerability, scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Choose two.)
Definitions:
Basic Sensations
The fundamental experiences generated by sensory stimuli, such as sight, sound, smell, touch, and taste.
Pressure
The force applied perpendicular to the surface of an object per unit area over which that force is distributed.
Basic Taste
The fundamental groups of taste perceived by humans, typically described as sweet, sour, salty, bitter, and umami.
Protein-Rich Foods
Edibles high in protein content, essential for body repair, growth, and overall health, such as meat, fish, eggs, and beans.
Q6: A client has voiced concern about the
Q49: Which of the following CPU registers does
Q56: An attacker performed a MITM attack against
Q68: The supervisor asks an engineer to be
Q71: A penetration tester is scanning a network
Q98: While performing privilege escalation on a Windows
Q145: Which of the following organization types requires
Q241: During a project, a key stakeholder asks
Q420: A project task has been completed ahead
Q490: A project manager is determining a project's