While reviewing the wireless router, the systems administrator of a small business determines someone is spoofing the MAC address of an authorized device. Given the table below: 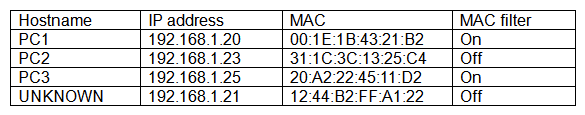 Which of the following should be the administrator's NEXT step to detect if there is a rogue system without impacting availability?
Which of the following should be the administrator's NEXT step to detect if there is a rogue system without impacting availability?
Definitions:
Chain Gangs
Groups of prisoners chained together to perform menial or physically challenging work as a form of punishment.
United States Marines
A division of the U.S. Military tasked with delivering swift power projection through the mobility offered by the U.S. Navy, enabling the rapid deployment of combined-arms task forces.
Haiti
A country in the Caribbean on the island of Hispaniola, notable for its rich culture, history of slavery, and being the site of the first successful slave rebellion that led to independence.
Stock Market
A public entity for the trading of company stocks and other securities, a key component of the global financial system.
Q84: A network technician is trying to determine
Q216: A company has a data system with
Q308: A systems administrator has isolated an infected
Q614: After being alerted to potential anomalous activity
Q660: A security analyst receives an alert from
Q846: An organization has decided to host its
Q851: A company recently replaced its unsecure email
Q933: A security auditor is testing perimeter security
Q1003: The IT department needs to prevent users
Q1009: To reduce disk consumption, an organization's legal