A user suspects someone has been accessing a home network without permission by spoofing the MAC address of an authorized system. While attempting to determine if an authorized user is logged into the home network, the user reviews the wireless router, which shows the following table for systems that are currently on the home network. 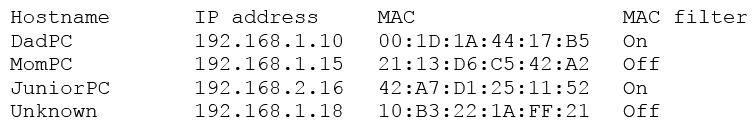 Which of the following should be the NEXT step to determine if there is an unauthorized user on the network?
Which of the following should be the NEXT step to determine if there is an unauthorized user on the network?
Definitions:
Web Browser
A Web Browser is a software application used to access information on the World Wide Web, presenting websites and navigating web content.
Object
An instance of a class containing both data (attributes) and functions (methods) that operate on the data.
Algorithm
A finite sequence of well-defined instructions typically used for solving a problem or performing a computation.
Analyzing The Problem
The process of understanding a problem completely and finding possible ways to solve it by breaking it down into smaller parts.
Q65: Which of the following characteristics differentiate a
Q93: A system in the network is used
Q110: A company stores highly sensitive data files
Q287: In highly secure environments where the risk
Q379: A cryptographer has developed a new proprietary
Q610: A company occupies the third floor of
Q624: A security analyst has been asked to
Q681: A new Chief Information Officer (CIO) has
Q696: Users report the following message appears when
Q1139: The security administrator receives an email on