A system administrator is reviewing the following information from a compromised server. 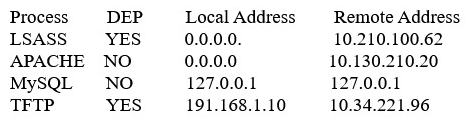 Given the above information, which of the following processes was MOST likely exploited via remote buffer overflow attack?
Given the above information, which of the following processes was MOST likely exploited via remote buffer overflow attack?
Definitions:
Incidental Damages
Additional costs incurred as a consequence of a breach of contract, beyond the direct damages or loss.
Lost Profits
Lost profits refer to the potential earnings a company or individual was unable to realize due to another party's wrongful acts or breaches of contract.
Defective Performance
The failure to meet the required or expected standards of performance in the execution of a contractual duty or obligation.
Computation of Damages
The process of calculating the amount of money that one party must pay to another as compensation for harm or loss caused by a breach of contract, negligence, or other wrongful act.
Q80: Which of the following is the proper
Q99: Which of the following is a team
Q147: Corporations choose to exceed regulatory framework standards
Q828: A systems administrator wants to implement a
Q883: A security analyst is reviewing the following
Q890: An analysis of a threat actor, which
Q920: A government agency with sensitive information wants
Q921: A company is allowing a BYOD policy
Q1020: A security analyst is investigating a call
Q1151: A Chief Information Officer (CIO) is concerned