A security analyst reviews the following output: 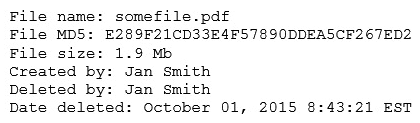 The analyst loads the hash into the SIEM to discover if this hash is seen in other parts of the network. After inspecting a large number of files, the security analyst reports the following:
The analyst loads the hash into the SIEM to discover if this hash is seen in other parts of the network. After inspecting a large number of files, the security analyst reports the following: 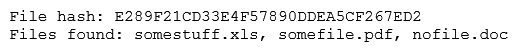 Which of the following is the MOST likely cause of the hash being found in other areas?
Which of the following is the MOST likely cause of the hash being found in other areas?
Definitions:
Social Contagion
The phenomenon where ideas, feelings, behaviors, or attitudes spread within a group or society, akin to the transmission of a disease.
Reference Group
A social group that serves as a point of comparison for individuals when forming attitudes or behaviors.
Normative Influence
The effect of societal norms on an individual's behavior, often leading to conformity.
Strongly Identifies
The intense connection or affinity an individual feels with a particular group, idea, or object.
Q31: A company has drafted an insider-threat policy
Q43: A security administrator suspects an employee has
Q61: Which of the following identity access methods
Q717: A company is having issues with intellectual
Q780: Before an infection was detected, several of
Q802: Which of the following provides PFS?<br>A) AES<br>B)
Q934: A help desk technician receives a phone
Q1040: A security analyst has identified malware that
Q1082: A security analyst wishes to scan the
Q1108: A root cause analysis reveals that a