After reading the paragraphs below, answer the questions that follow.
A technique called flow cytometry is used by scientists and researchers to count or sort cells based on specific properties. By labeling cellular DNA with a fluorescent dye, flow cytometry can sort cells based on the amount of DNA present, thereby making it possible to distinguish between cells that are in different stages of the cell cycle. Flow cytometry is especially useful to the medical community because it can help with the diagnosis of certain types of cancers.
Below is a typical set of data that you might obtain when running a flow cytometry experiment using a sample of healthy skin cells. Use this figure to help you answer the following questions.
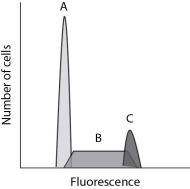
-Which peak corresponds to cells in G₁? In S phase? In G₂?
Definitions:
Encryption
The method of transforming data or information into a secret code to protect it from unauthorized entry.
Digital Certificate
A digital form of identification issued by a trusted authority to verify the authenticity of an entity or device online.
Password
A secret word or phrase used to verify the identity of a user during the authentication process.
Two-factor Authentication
An enhanced security process requiring two different forms of identification from the user before granting access to an account or system.
Q7: Research since Mendel's time has established that
Q18: Which of the following statements regarding cross-breeding
Q20: Wood frogs freeze solid during the winter
Q42: Which of the following statements regarding RNA
Q42: Two yeast cells, one of type a
Q46: A colorblind woman marries a man who
Q52: Female inheritance patterns cannot be analyzed by
Q53: The shape of a DNA molecule is
Q59: Which of the following statements regarding mitosis
Q66: A signal outside a cell triggers changes