True/False
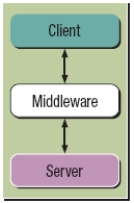
-The figure above shows an n-tier database model.
Identify the shift in media engagement and content creation from traditional to digital platforms.
Analyze the role and impact of audience interpretation in the reception of mass media.
Examine the concept of "No Comment" in Ms. magazine as a critique of sexism in media.
Explain the importance of racialized digital spaces, like "Black Twitter," in promoting cultural identity and social discussion.
Definitions:
Related Questions
Q7: The C2C model is also known as
Q10: Name three ways that articles published in
Q13: The text mentions two important questions to
Q44: Objects stored in an OODBMS can be
Q44: Phishing schemes use legitimate-looking e-mails to trick
Q55: Data definition involves describing the properties of
Q60: The process of evaluating and correcting the
Q91: Most DBMSs come bundled with a set
Q94: With _,the computer uses each record's primary
Q98: Although there is no precise definition of