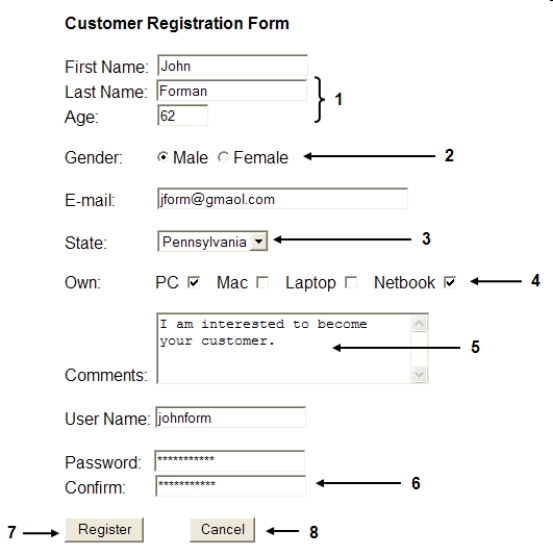
-Given the item marked 3 in the accompanying figure,the Pennsylvania option has been marked with the ____ attribute.
Definitions:
Authentication Factors
The various methods used to verify the identity of a user, device, or entity, including something you know, something you have, and something you are.
Unsolicited E-mail
Email received without the recipient's prior request or consent, often considered spam.
Antivirus Software
Programs designed to detect, prevent, and take action to disarm or remove malicious software programs, such as viruses and worms from computers.
Viruses
Malicious software programs designed to replicate and spread, while potentially causing damage to data and systems.
Q7: The criteria on which juvenile sentencing is
Q19: Radio buttons are also known as _
Q24: What is the value of the media
Q33: Which of the following does James tell
Q51: The box marked 3 in the accompanying
Q76: In a fixed-width layout,the _ of columns
Q84: The _ attribute serves as the heading
Q89: Research that links antisocial behavior to a
Q130: Ethan is trying to use the max-width
Q130: Which of the following tags is optional