Figure 2.15 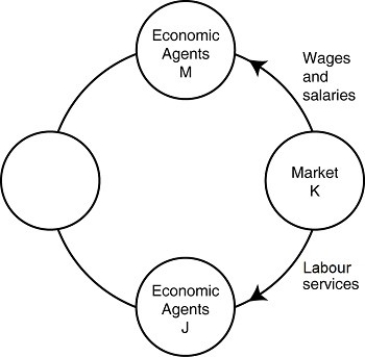 Alt text for Figure 2.15: In figure 2.15, a circular flow diagram.
Alt text for Figure 2.15: In figure 2.15, a circular flow diagram.
Long description for Figure 2.15: 4 circles arranged in a circle, labelled as follows, clockwise from the top center: Economic Agents M, Market K, and Economic Agents J.The fourth circle is empty unmarked.The diagram shows the flow of wages and salaries from Market K to Economic Agents M.The flow of labor services goes from Market K to Economic Agents J.
-Refer to Figure 2.15.One segment of the circular flow diagram in the figure shows the flow of labour services from market K to economic agents J.What is market K and who are economic agents J?
Definitions:
Tailgating
An unauthorized person following an authorized individual to gain entry into a restricted area, often used in the context of security breaches.
Unauthorized Person
An individual who does not have the necessary approvals or permissions to access a specific area, system, or set of information.
Authorized Person
An individual who has been officially granted permission or authority to access specific resources, areas, or information, often within a restricted or secure environment.
Spear Phishing
A targeted type of social engineering in which the attackers know some information about someone that lulls them into thinking an email or other electronic message is safe.
Q1: Which of the following would shift a
Q3: A tolerance limit is what the customer
Q17: A normal good is a good for
Q33: Describe at least three alternative approaches to
Q78: Refer to Table 1.1.What is Lydia's marginal
Q88: Which of the following would cause an
Q105: Arlene quits her $125,000-a-year job to take
Q107: Alberta ranchers can raise either cattle or
Q199: The production possibilities frontier shows<br>A)the various products
Q212: Izzy Amador is a highly talented tattoo