Use the tables for the question(s) below.
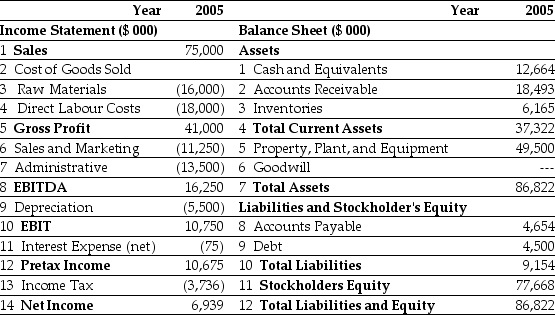
Estimated 2005 Income Statement and Balance Sheet Data for Ideko Corporation
 The following are financial ratios for three comparable companies:
The following are financial ratios for three comparable companies:
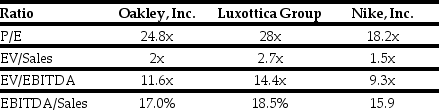
-Based upon the average EV/EBITDA ratio of the comparable firms,Ideko's target economic value is closest to:
Definitions:
PXE
Preboot eXecution Environment, a technology that allows computers to boot up using software received through a network, without the need for storage devices.
NFC
Near Field Communication (NFC) is a short-range wireless connectivity technology allowing for secure communication between devices over a distance of a few centimeters.
Internet Explorer
A discontinued web browser developed by Microsoft, once the default browser for Windows, known for its role in the early web but replaced by Microsoft Edge.
Malware
Malicious software designed to damage, disrupt, or gain unauthorized access to computer systems and data.
Q3: Following the borrowing of $12 million and
Q5: The futures prices for oil are determined
Q8: The effective dividend tax rate for a
Q9: The unlevered beta for Oakley is closest
Q23: The amortization expense may be used for
Q35: What is the difference between inside,gray,and outside
Q37: Which of the following statements regarding capital
Q55: Assuming Luther issues a 5:2 stock split,then
Q77: The three main methods of capital budgeting
Q95: Assume that capital markets are perfect,you issue