Table 11.2
Computer Disk Duplicators, Inc. has been considering several capital investment proposals for the year beginning in 2004. For each investment proposal, the relevant cash flows and other relevant financial data are summarized in the table below. In the case of a replacement decision, the total installed cost of the equipment will be partially offset by the sale of existing equipment. The firm is subject to a 40 percent tax rate on ordinary income and on long-term capital gains. The firm's cost of capital is 15 percent.
__________________________________________________________ 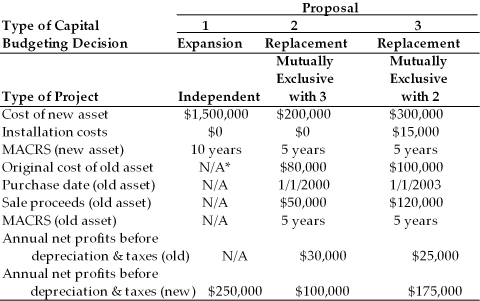 *Not applicable
*Not applicable
-For Proposal 3, the annual incremental after-tax cash flow from operations for year 3 is ________. (See Table 11.2)
Definitions:
UPS
Uninterruptible Power Supply; a backup power device that provides immediate power to connected equipment when the primary power source fails.
Spoofing
Sending an Ethernet frame with a fake source MAC address to trick other devices into sending traffic to a rogue device.
DoS
Denial of Service, a type of cyber attack aimed at making a network service unavailable to its intended users by overwhelming it with excessive requests.
Shoulder Surfing
The practice of spying on someone's personal information by looking over their shoulder, often used to gain unauthorized access to passwords or other sensitive information.
Q6: The objective of _ is to select
Q9: Because risk premiums increase with increases in
Q12: Operating leverage measures the effect of fixed
Q32: In evaluating a proposed project, incremental operating
Q43: If vector <img src="https://d2lvgg3v3hfg70.cloudfront.net/TB2295/.jpg" alt="If vector
Q44: The NPV of an project with an
Q54: Tangshan Mining Company has released the following
Q85: The controller is commonly responsible for<br>A) managing
Q99: Companies involved in international capital budgeting projects
Q124: Johnson, Inc. has just ended the calendar