Exhibit 10.9.A tutor promises to improve GMAT scores of students by more than 50 points after three lessons.To see if this is true,the tutor takes a sample of 49 students' test scores after and before they received tutoring.The mean difference was 53 points better after tutoring,with a standard deviation of the difference equal to 12 points.Let 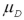 denote the mean of the difference: score after tutoring minus score before tutoring. Refer to Exhibit 10.9.Calculate the value of the test statistic.
denote the mean of the difference: score after tutoring minus score before tutoring. Refer to Exhibit 10.9.Calculate the value of the test statistic.
Definitions:
Synergy
The increased effectiveness or achievement that results when individuals or groups work together compared to when they work separately.
Stereotyping
The act of ascribing a fixed, oversimplified, and often exaggerated or prejudiced image or idea to a person or group.
Win-Win
A situation or outcome where all parties involved gain or achieve benefit.
Gender Egalitarianism
The belief in the equality of all genders, advocating for equal rights, responsibilities, and opportunities.
Q11: The starting salary of an administrative assistant
Q19: A 90% confidence interval is constructed for
Q24: Exhibit 8-5.A sample of 2,007 American adults
Q41: Exhibit 10.7.A stats professor at a large
Q70: Consider the following regression results based on
Q87: In the estimation of a multiple regression
Q88: A soft drink company fills two-liter bottles
Q89: A local courier service advertises that its
Q101: A city is considering widening a busy
Q108: Exhibit 8-6.A sample of 1400 American households