Using the critical numbers of 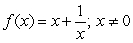 , use the Second Derivative Test to determine all local extrema.
, use the Second Derivative Test to determine all local extrema.
Definitions:
Security
Measures and protocols implemented to protect information, networks, and computer systems from unauthorized access, attacks, or theft.
Wireless Networks
Wireless Networks allow devices to connect and communicate with each other using radio waves, without the need for a physical connection, e.g. Wi-Fi networks.
Rogue Access Point
An unauthorized access point to a wireless network, which can pose security risks.
Unauthorized
Refers to actions taken or access granted without official permission or approval.
Q18: Evaluate the integral. <img src="https://d2lvgg3v3hfg70.cloudfront.net/TB2342/.jpg" alt="Evaluate the
Q32: Find the location of all horizontal and
Q33: List the points A, B, C, D,
Q48: A volume discount on a certain item
Q52: Evaluate the derivative using properties of logarithms
Q84: Evaluate the iterated integral. <img src="https://d2lvgg3v3hfg70.cloudfront.net/TB2342/.jpg" alt="Evaluate
Q88: Find all points at which <img src="https://d2lvgg3v3hfg70.cloudfront.net/TB2342/.jpg"
Q108: Find an antiderivative by reversing the chain
Q129: Use the Integral Mean Value Theorem to
Q141: Using the position function <img src="https://d2lvgg3v3hfg70.cloudfront.net/TB2342/.jpg" alt="Using