Figure 17-3 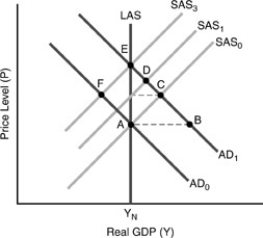
-In the figure above, SAS0 must shift to SAS1 when
Definitions:
Attacker
An individual or entity that attempts to gain unauthorized access to computer systems, networks, or data, often with malicious intent.
Agile Development
A methodology in software development that emphasizes flexibility, customer involvement, and iterative progress, allowing for rapid adjustments based on feedback.
Design Phase
A stage in project development focused on creating plans, specifications, and creative solutions before actual implementation begins.
Development Methodology
A structured framework used during the process of software development to plan, control, and manage the creation of a system or application.
Q10: The data in the customer master are
Q10: Replacing the simple Keynesian consumption function with
Q15: _ provides tools to manage and store
Q16: Which of the following statements regarding customer
Q24: The flaw of the Real Business Cycle
Q29: A reduction in the user cost of
Q30: Accounts payable is used to track money
Q54: A policy of maintaining a fixed interest
Q114: Which of the following statements best describes
Q132: The advantage of a nominal anchor is