Identify the conic by writing the equation in standard form. 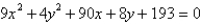
Definitions:
Bulleted List
A list of items preceded by bullet points, used to organize information in a clear and concise manner.
Social Engineering
A manipulation technique that exploits human error to gain private information, access, or valuables, often used in cybersecurity attacks.
Cyberattack
Malicious attempts to damage, disrupt, or gain unauthorized access to computer systems, networks, or devices.
Valuable Information
Data or facts that hold significant importance or worth to the user, often aiding in making informed decisions.
Q16: Which of the following is a zero
Q23: Write the equation <img src="https://d2lvgg3v3hfg70.cloudfront.net/TB8632/.jpg" alt="Write the
Q61: Solve <img src="https://d2lvgg3v3hfg70.cloudfront.net/TB8632/.jpg" alt="Solve by
Q75: Find the standard form of the equation
Q90: Find the inverse of the one-to-one function.
Q100: Find all the rational zeros of the
Q101: Solve: <img src="https://d2lvgg3v3hfg70.cloudfront.net/TB8632/.jpg" alt="Solve: A)
Q104: Graph the hyperbola. <img src="https://d2lvgg3v3hfg70.cloudfront.net/TB8632/.jpg" alt="Graph the
Q109: Let <img src="https://d2lvgg3v3hfg70.cloudfront.net/TB8632/.jpg" alt="Let .
Q127: In skeletal muscle, the thick filaments are