When Service A receives a message from Service Consumer A(1) ,the message is processed by Component A. This component first invokes Component B (2) , which uses values from the message to query Database A in order to retrieve additional data. Component B then returns the additional data to Component A. Component A then invokes Component C (3) , which interacts with the API of a legacy system to retrieve a new data value. Component C then returns the data value back to Component A. Next, Component A sends some of the data it has accumulated to Component D (4) , which writes the data to a te>X file that is placed in a specific folder. Component D then waits until this file is imported into a different system via a regularly scheduled batch import. Upon completion of the import, Component D returns a success or failure code back to Component A. Component A finally sends a response to Service Consumer A (5) containing all of the data collected so far and Service Consumer A writes all of the data to Database B (6) . Components A, B, C. and D belong to the Service A service architecture. Database A, the legacy system, and the file folders are shared resources within the IT enterprise. 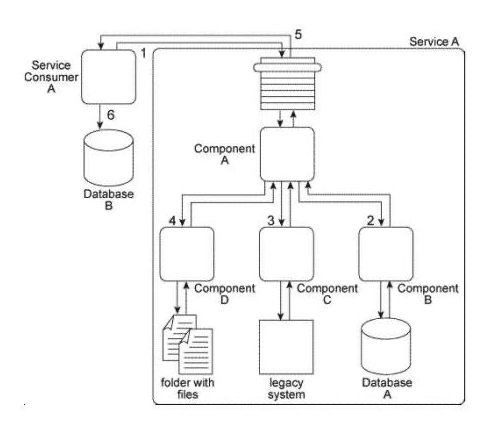 Service A is an entity service with a service architecture that has grown over the past few years. As a result of a service inventory-wide redesign project, you are asked to revisit the Service A service architecture in order to separate the logic provided by Components B, C, and D into three different utility services without disrupting the behavior of Service A as it relates to Service Consumer A . What steps can be taken to fulfill these requirements?
Service A is an entity service with a service architecture that has grown over the past few years. As a result of a service inventory-wide redesign project, you are asked to revisit the Service A service architecture in order to separate the logic provided by Components B, C, and D into three different utility services without disrupting the behavior of Service A as it relates to Service Consumer A . What steps can be taken to fulfill these requirements?
Definitions:
Computer-Aided Manufacturing
A form of automation where computer software controls machinery and manufacturing processes.
Manufacturing Processes
The methods and procedures used in the transformation of raw materials into finished goods or products.
Computers
Electronic devices capable of executing programmed instructions to perform a wide range of tasks from simple calculations to complex computing.
Malware
Software intentionally designed to cause damage to a computer, server, client, or computer network.
Q9: Which feature would be used for SAN
Q13: Which two statements about jumbo Ethernet frames
Q33: The application of the Redundant Implementation pattern
Q34: Click the Exhibit button. <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1984/.jpg" alt="Click
Q43: Assume you have product with qty in
Q54: What limits the repurchase price to a
Q55: The enforcement of service contract design standards
Q65: Which of the following id NOT the
Q82: Which two types of data does Orion
Q110: A metric is a measurement standard or