A user suspects someone has been accessing a home network without permission by spoofing the MAC address of an authorized system. While attempting to determine if an authorized user is logged into the home network, the user reviews the wireless router, which shows the following table for systems that are currently on the home network. 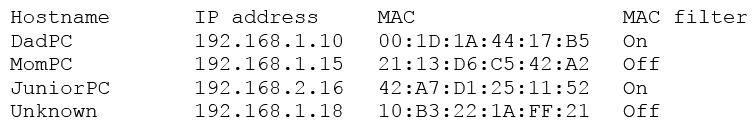 Which of the following should be the NEXT step to determine if there is an unauthorized user on the network?
Which of the following should be the NEXT step to determine if there is an unauthorized user on the network?
Definitions:
Code Of Ethics
A set of principles and guidelines designed to help professionals conduct their business with integrity and honesty.
Project Management Institute
An international professional organization for project management professionals, offering certifications, resources, and advocacy.
Work Breakdown Structure
A hierarchical description of a project into more and more detailed components.
Q67: An external auditor visits the human resources
Q84: A network technician is trying to determine
Q363: A malicious actor compromises a legitimate website,
Q528: A security engineer must install the same
Q665: Joe, a contractor, is hired by a
Q723: A vice president at a manufacturing organization
Q725: When attackers use a compromised host as
Q777: After attempting to harden a web server,
Q1023: A company has noticed multiple instances of
Q1035: A developer has just finished coding a