A security administrator is implementing a new WAF solution and has placed some of the web servers behind the WAF, with the WAF set to audit mode. When reviewing the audit logs of external requests and posts to the web servers, the administrator finds the following entry: 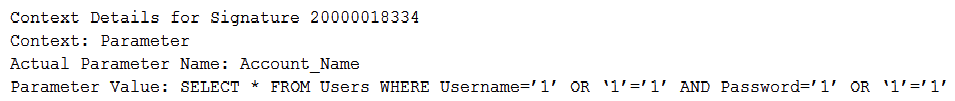 Based on this data, which of the following actions should the administrator take?
Based on this data, which of the following actions should the administrator take?
Definitions:
Societal Culture
Societal culture refers to the shared values, norms, and practices that characterize a society.
Organizational Culture
The shared values, beliefs, and practices that shape the social and psychological environment of a business or organization.
Collective Experience
Shared experiences or knowledge among a group of individuals, contributing to a common understanding or culture.
Larger Environment
The broader context or setting, including natural, social, economic, and political factors, that influences or shapes the actions and outcomes of individuals or organizations.
Q206: During an application design, the development team
Q246: An organization has implemented an IPSec VPN
Q386: A server technician is examining reports of
Q652: A systems administrator is installing a new
Q717: A company is having issues with intellectual
Q758: An administrator has concerns regarding the traveling
Q772: While reviewing the monthly internet usage it
Q858: A user loses a COPE device. Which
Q1051: Joe, a backup administrator, wants to implement
Q1124: A security administrator has been tasked with