REFERENCE: Ref.03_14
Jaynes Inc.obtained all of Aaron Co.'s common stock on January 1,2009,by issuing 11,000 shares of $1 par value common stock.Jaynes' shares had a $17 per share fair value.On that date,Aaron reported a net book value of $120,000.However,its equipment (with a five-year remaining life)was undervalued by $6,000 in the company's accounting records.Any excess of consideration transferred over fair value of assets and liabilities is assigned to an unrecorded patent to be amortized over ten years.
SHAPE \* MERGEFORMAT
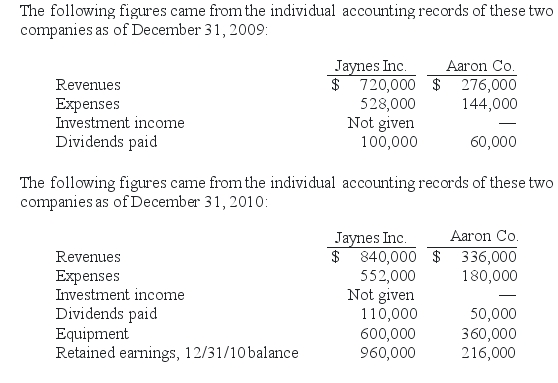
-If this combination is viewed as an acquisition,what balance would Jaynes' Investment in Aaron Co.account have shown on December 31,2010,when the equity method was applied?
Definitions:
Intranet
A private network accessible only to an organization's staff, often containing company-specific tools and resources.
Transport Layer Security
A cryptographic protocol designed to provide secure communication over a computer network.
Credit Card
A payment card issued to users as a method of payment allowing the cardholder to pay for goods and services based on the cardholder's promise to pay for them.
Whitelisting
A process in which a company identifies acceptable software and permits it to run, and either prevents anything else from running or lets new software run in a quarantined environment until the company can verify its validity.
Q9: Under modified accrual accounting,revenues should be recognized
Q19: What amount of goodwill should be attributed
Q29: Goodwill is often created,or purchased,during a business
Q39: The Town of Anthrop has recorded the
Q47: Chapel Hill Company had common stock of
Q48: During 2009,Parent Corporation purchased at book value
Q53: Compute the amount of Hurley's land that
Q56: Administrative expenses of $13,000 were paid.<br>Prepare the
Q71: Compute the gain on transfer of equipment
Q72: For a government,what kind of operations are